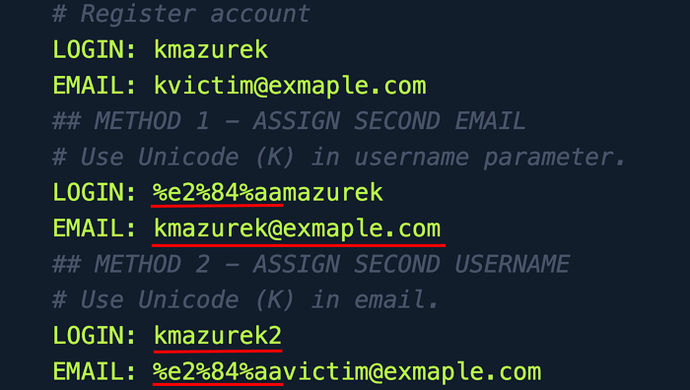
This question is specifically regarding Unicode Normalization / Account Takeover on registration forms.
Does Wappler automatically handle ensuring canonical encoding is used across all the text and that no invalid characters are present? or is this something that needs to be manually configured?
The validator should not accept double registration with Unicode signs.
Register account with Unicode letter. As an example:
U+0212A normalizes to K and can be sent URL encoded as %e2%84%aa.
- List item An attacker could use this to hijack an existing account by creating the same one with Unicode characters and assigning different sign-in components (email/username/phone number etc.)
- List item Records in the database of the old account could be overwritten, which could allow logging in using the new password.