So, I am looking to replace my existing login which was added in DreamWeaver and now use the Server Connect Security to log in the user.
My old DW login used the following,
MM_loginSQL = "SELECT strUserName, strUserPassword"
If MM_fldUserAuthorization <> "" Then MM_loginSQL = MM_loginSQL & "," & MM_fldUserAuthorization
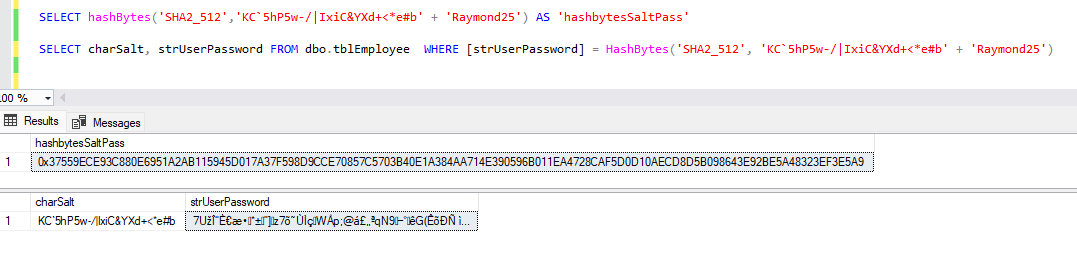
MM_loginSQL = MM_loginSQL & " FROM dbo.tblEmployee WHERE strUserName = ? AND strUserPassword =HashBytes('SHA2_512', [charSalt] + ?) AND intEmployeeActive = 1"
Set MM_rsUser_cmd = Server.CreateObject ("ADODB.Command")
MM_rsUser_cmd.ActiveConnection = MM_PaymentPlusCRM_STRING
MM_rsUser_cmd.CommandText = MM_loginSQL
MM_rsUser_cmd.Parameters.Append MM_rsUser_cmd.CreateParameter("param1", 200, 1, 30, MM_valUsername) ' adVarChar
MM_rsUser_cmd.Parameters.Append MM_rsUser_cmd.CreateParameter("param2", 200, 1, 30, Request.Form("password")) ' adVarChar
MM_rsUser_cmd.Prepared = true
Set MM_rsUser = MM_rsUser_cmd.Execute
You will see it validated the user using WHERE strUserName = (Username inputted into the form) AND strUserPassword =HashBytes('SHA2_512', [charSalt] + (Password inputted into the form))
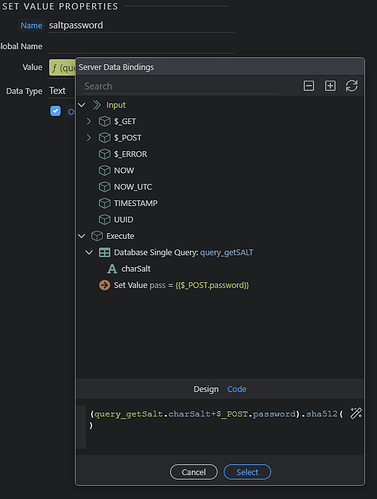
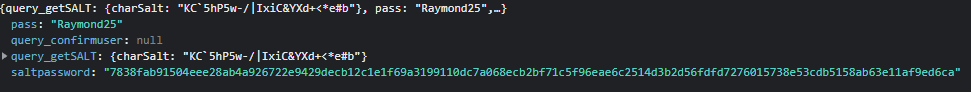
I first get the Salt value from the DB for the user as this value is different for every user.
I tried query_getSalt.charSalt + $_POST.password.sha512() and I keep getting Unauthorized.
How would I replicate this HashBytes for the login?
Thanks
Ray