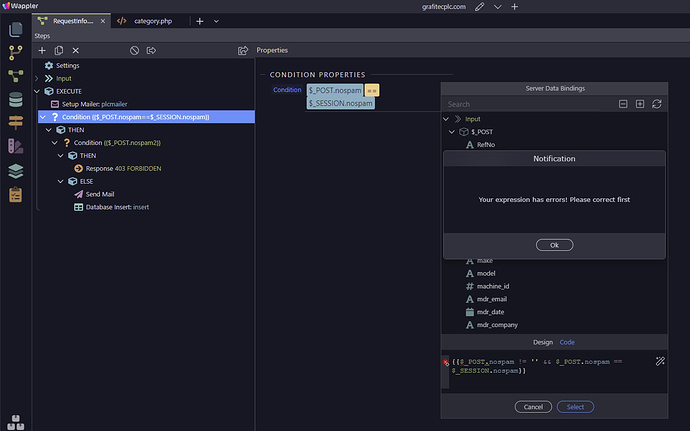
I tried that but got an error so I removed the {{ }}
It should be entered without the {{ }} around. try changing the expression to:
$_POST.nospam && $_POST.nospam==$_SESSION.nospam instead
So if I send a request the only thing that comes through is a Russian spam email, somehow someone has figured how to alter or hack the function pages!!!
The expression you gave results in no email coming through.
How can I get rid of this?
So if I send a request the only thing that comes through is a Russian spam email, somehow someone has figured how to alter or hack the function pages!!!
Sorry but i really have no idea what are you talking about.
The expression checks if the nospam input has a value or not. Which means if the server action is not run through the form it wont send a value.
What I trying to explain is, when I try sending a request from the website using the form, some how I’m getting several emails through from a Russian spammer, it looks like something within the sending function has been hacked!
I don’t get any email information from the form, only the random spam details.
Where do I start to look for how the send mail function has been compromised.
I have changed the sending/relaying smtp account and its password but that hasn’t stopped it so must presume something else is attaching to the site or function pages and hijacking and request made from the site.
First of all change your ftp details (i suppose you are using ftp), as this is most probably the issue, then check the latest files modified on your server. Check the form page for scripts or weird code injected.
Maybe also provide a link where we can check it as well.
I’ve changed the ftp username and password, also checked any files that have been changed but this issue has been going on for some time but never to this extent.
How can I send you the ftp details so your able to see if you can find whats going on?
You can send me a personal message here in the forum.
will be interesting to see what the issue is.
Hi gunnery, while Teodor is looking at your issue, it just reminded me some similar issue with who was receiving each day lot of spam emails from a specific country (I think it was Lithuania)…I first blocked the email address in the host admin (cPanel in my case) but the sender was using many different addresses so I decided to look for the main internet provider (s) for that country and found their IP so I blocked those IP in cPanl and that stooped the spamming all from that country, this could be at least a temporary fix so you don’t get tons of spam email from that country while finding a permanent solution, hope this can be of any help 
With things like missing fields, I am wondering if the spammer is using the the API function. Are they sending emails directly from their own server because they managed to harvest the email address from the website? Many moons ago, I was receiving about 2500 emails a day from a spammer. Fortunately these were addressed to info@. In Plesk, I fixed it so that info@ would repel any incoming emails. Problem solved.
Even now, I see many websites that have the mailto link as in
<a href="mailto:name@theirsite.com">Send mail</a>
This is breakfast, lunch and dinner for email harvesters. Don’t be surprised by getting a bunch of spam.
I have created a video on the subject which may be helpful.
Thank you all for your replies.
Although Teodor has been through everything on the website and found not injection code I think this spammer is directly using the API.
Because we use Office365 Exchange I have to have a dummy domain in plesk that I use to relay the emails through otherwise it tries to deliver the mail to the localhost. As soon as I delete this dummy domain the spam stops, however if I create a new dummy domain with different credentials, as soon as I send one request from my website the spam immediately starts! I have other sites using the same dummy domain smtp and they are not getting any spam so I’m guessing there is something out there thats watching the API of the domain concerned and as soon as a form is send it somehow starts spamming directing as you suggest the API.
I’d like to directly use O365 and I have read through the post of @vfn Email Not sending - hellllpppp
but for me the emails won’t go through. I’m a little confused as to how to get the more detailed error message out, all I get in the browser inspect is server error 500.
Lastly, the php function I used to use before DMX and Wappler had an anti spam function in the send script which checked to see if the function was being used locally of from another IP address, perhaps this is something that needs to be added to Wappler Send Mail?
By way of an update my ISP has checked everything at their end and found nothing.
I re-created the API file with a different name and used a 3rd party smtp company and the spamming has stopped. I can only presume something targeted/found the API file, remembered it name and somehow everytime I used it started sending spam through it directly!
Am I right in thinking no anti-spam measures on the actual form page would have stopped this and what in the future can be done to stop it happening again?
Yes…and no. The more anti-spam measures you enforce means that the spammer might just look for another victim and leave you alone.
You should protect you API endpoint as much as you can, but know that nearly all restrictions can be circumvented.
- Restrict origin header
- Rate limit it
- Log IP of who is calling it and block automatically if it goes over the rate limit.
Thanks @JonL, can you direct to any info pages on how to implement the options you gave above?
If the API call has properly setup honeypots then even calling the API directly should keep them out.
I will be publishing a module next week convering spammer protection (it’s in post production) which should protect the API action against being called directly
Maybe it’s worth to wait for Brian’s tutorial as it will be a step-by-step.
Way better than me pasting a bunch of Stackoverflow links where you won’t be well received if you have questions because SO is one hell of a shit show 
In any case the first line of defence should be rate limiting as it’s the only effective thing you can do to stop API abuse. Unfortunately you are using PHP and I am not versed on php packages for rate limiting.
3 posts were split to a new topic: Implement Server Connect rate limiting
Sounds great Brian, looking forward to watching it…
Released 8 modules of the new Wappler 5 course, bit earlier than i had planned but that’s life Still lots more to follow but though I should at least release up to the modules covering honeypots and spam protection. The technique is used on a registration form but would be exactly the same for a contact form.
The 2 modules are those headed Spam Bot and Registration Bot Protection which cover the blank honeypot and the coded honeypot.
Playlist: https://www.youtube.com/playlist?list=PLUjqTJN3byC9W9UFjsV9f9vefe_ZSFQfb