Is there a way with medium editor to not allow links to be added in there to try and reduce spam.
I have a client who hates the captcha’s, but does not want as much spam.
Any suggestions??
Please check:
I also often used such a honeypot, works perfectly. I used it in a bit different way a bit more secure. I generated a random hash with asp/php, stored that in a session and then used that as value in a hidden field, after form submit I then check on the server if the value is the same as the one in the session.
Thank you @patrick, this is the perrrfect solution. 
Cheers that did the job
Great solution as well  cheers
cheers
Deploying now to a few contact forms I have Live. Thanks Patrick!
Any chance of a little tutorial or a few screen shots to show how to do this?
You first need to create the session and a random value for it, not sure what did @patrick use for this, but this will do the job fine:
<?php
session_start();
$_SESSION['honey'] = md5(uniqid(rand(), true));
?>
Make sure to place it before the opening <html> tag. This will generate a new value on each page refresh.
Then in your honeypot field use the session as a value:
<input type="text" name="inp_honey" id="inp_honey" value="<?php echo $_SESSION['honey'] ?>" autocomplete="off"/>
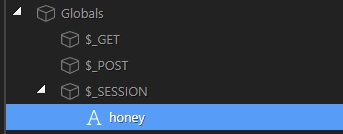
On the server side add the session under Globals > $_SESSION:
In the condition check if the honeypot $_POST equals the $_SESSON variable, the rest is the same as in the tutorial i linked:
{{$_POST.inp_honey == $_SESSION.honey}}
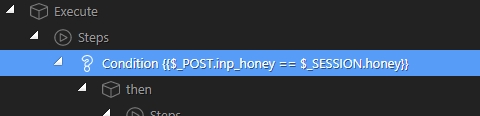
So, if the honeypot input value changes in any way, the condition will be false.
I’m sure works very well and is a good solution. I’m just wondering if a robot would be less inclined to fill in a field which already had a default value. Might it not be more tempted to fill in only blank fields - including the honey-pot field? (As far as robots are ‘tempted’ to do anything.)
Just duplicate the honey pot ( say honeypot2) leave it blank and check in server action that it is still blank on submission. That way you cover both angles.
There would certainly be an option to make it even more secure.
I mentioned in a thread a year ago that I had used this technique for a while and had no reports from the customer that he had received any spam. This is still the case and I’ve received about 1800 messages from the server to date, informing me that a robot has used the form.
Have to say, great result with this solution… not one bit of spam today. 
Hi
How do I check if my {{$_POST.name-honey}} has a value, can someone give the steps in the server action please?
CK
Use the Condition action where the condition is your post variable.
As in {$_POST.name-honey==$_POST.name-honey}} ?
Just {{$_POST.name-honey}} should do it.
If there’s a value it will return true and do the THEN actions, if empty it will be false and do the ELSE actions
OK, thank you.
Finally, where is the set status action, I can’t seem to find it in the actions menu?
It’s under Core Actions and it is called Response.
Thank you