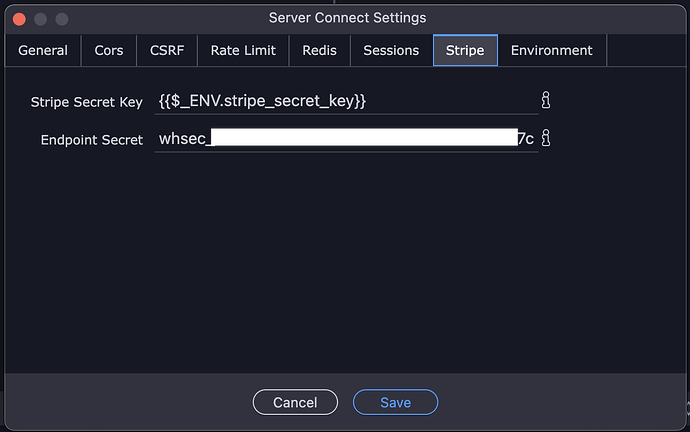
I'm aware that Stripe secret keys and endpoint keys are saved 'per target' in the Server Connect Settings. What I'm not aware of is how safe/unsafe this practice is. Some posts suggest creating environment variables for these keys and referencing the keys in each target's Server Connect Settings like {{$_ENV.stripe_secret.key}}. This requires putting the actual keys into the Environment tab, also in Server Connect Settings.
What are the risks of putting the keys directly into the Stripe tab?
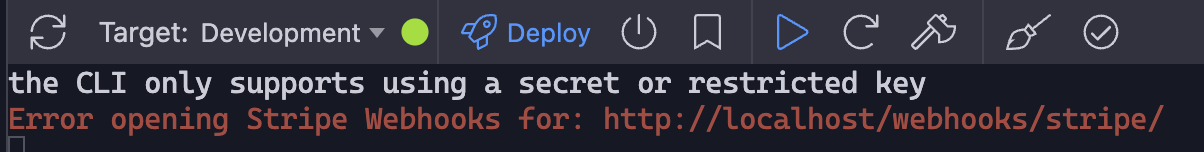
I can tell you that the Stripe CLI in Wappler does not work when using environment variables in place of the hard coded keys. You'll get the following output when trying to test a Stripe webhook: