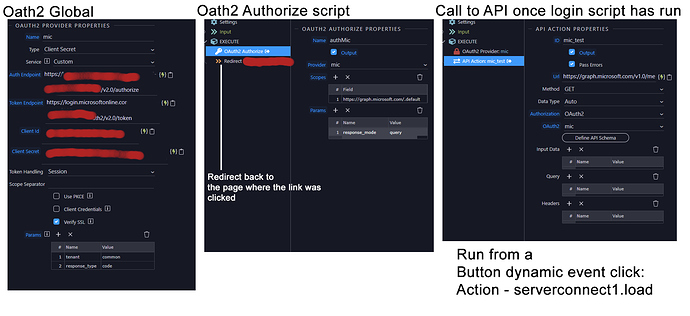
Header information from serverconnect mgraph_test.php file
GENERAL
Request URL: https://www.mysite.co.uk/SLSDatabase/dmxConnect/api/mgraph_test.php?
Request Method: GET
Status Code: 302
Remote Address: 217.160.0.190:443
Referrer Policy: strict-origin-when-cross-origin
RESPONSE HEADERS
access-control-allow-credentials: true
access-control-allow-origin: *
cache-control: no-store
content-type: text/html; charset=UTF-8
date: Wed, 15 Mar 2023 15:25:16 GMT
expires: Thu, 19 Nov 1981 08:52:00 GMT
location: https://login.microsoftonline.com//oauth2/v2.0/authorize?blablabla
pragma: no-cache
server: Apache
set-cookie: PHPSESSID=29e353b25b5a40337821d449d41f3fe0; path=/; secure; HttpOnly; SameSite=None
vary: Origin
REQUEST HEADERS
:method: GET
:path: https://www.mysite.co.uk/SLSDatabase/dmxConnect/api/mgraph_test.php?
:scheme: https
accept: application/json
accept-encoding: gzip, deflate, br
accept-language: en-US,en;q=0.9,la;q=0.8
cache-control: no-cache
pragma: no-cache
referer: refering page
sec-ch-ua: “Google Chrome”;v=“111”, “Not(A:Brand”;v=“8”, “Chromium”;v=“111”
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: “Windows”
sec-fetch-dest: empty
sec-fetch-mode: cors
sec-fetch-site: same-origin
user-agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
Header information from https://login.microsoftonline.com//oauth2/v2.0/authorize?blablabla
Request URL: https://login.microsoftonline.com//oauth2/v2.0/authorize?blablabla
Request Method: GET
Status Code: 200 OK
Referrer Policy: strict-origin-when-cross-origin
RESPONSE HEADERS
Cache-Control: no-store, no-cache
Content-Encoding: gzip
Content-Length: 55308
Content-Type: text/html; charset=utf-8
Date: Wed, 15 Mar 2023 15:25:16 GMT
Expires: -1
nel: {“report_to”:“network-errors”,“max_age”:86400,“success_fraction”:0.001,“failure_fraction”:1.0}
P3P: CP=“DSP CUR OTPi IND OTRi ONL FIN”
Pragma: no-cache
Referrer-Policy: strict-origin-when-cross-origin
report-to: {“group”:“network-errors”,“max_age”:86400,“endpoints”:[{“url”:“https://identity.nel.measure.office.net/api/report?catId=GW+estsfd+ams2”}]}
Set-Cookie: fpc=AlF5FttAntFInfRS1uPq5WU; expires=Fri, 14-Apr-2023 15:25:16 GMT; path=/; secure; HttpOnly; SameSite=None
Set-Cookie: x-ms-gateway-slice=estsfd; path=/; secure; samesite=none; httponly
Set-Cookie: stsservicecookie=estsfd; path=/; secure; samesite=none; httponly
Strict-Transport-Security: max-age=31536000; includeSubDomains
Vary: Accept-Encoding
X-Content-Type-Options: nosniff
x-ms-ests-server: 2.1.14711.7 - NEULR2 ProdSlices
x-ms-request-id: d06dcfc7-bd7d-45ae-9693-9ea975d67800
X-XSS-Protection: 0
REQUEST HEADERS
accept: application/json
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9,la;q=0.8
Cache-Control: no-cache
Connection: keep-alive
Host: login.microsoftonline.com
Origin: https://www.mysite.co.uk
Pragma: no-cache
Referer: https://www.mysite.co.uk/
sec-ch-ua: “Google Chrome”;v=“111”, “Not(A:Brand”;v=“8”, “Chromium”;v=“111”
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: “Windows”
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
Error message
Access to XMLHttpRequest at ‘https://login.microsoftonline.com//oauth2/v2.0/authorize?blablabla’ (redirected from 'https://www.mysite.co.uk/SLSDatabase/dmxConnect/api/mgraph_test.php?’) from origin ‘https://www.mysite.co.uk’ has been blocked by CORS policy: No ‘Access-Control-Allow-Origin’ header is present on the requested resource.
Hope this helps?
If you need any more information just let me know.
I can see there is no access-control-allow-origin: header from https://login.microsoftonline.com//oauth2/v2.0/authorize?blablabla but I have no control over that?
If I run https://www.mysite.co.uk/SLSDatabase/dmxConnect/api/mgraph_test.php? directly it works fine.
Many thanks Jon