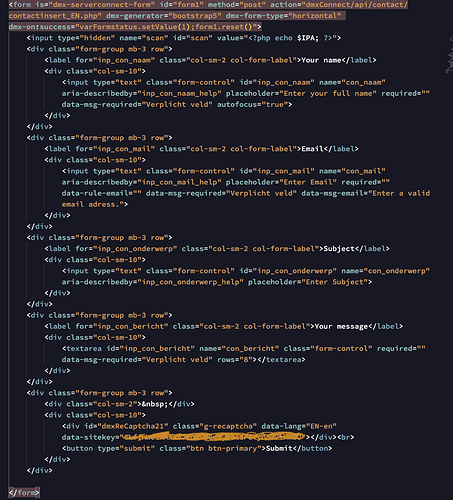
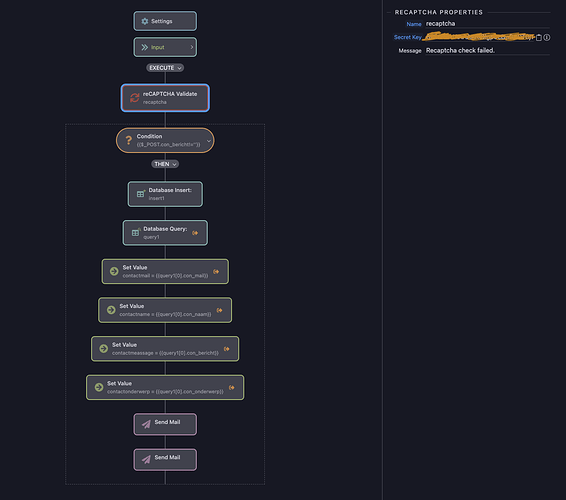
Hi, I have a contact form on the public site. On submit the server connect form triggers the server connect api. This api stores the form POST data in a database, and after saving sends out two emails. For some time now, people looked up the form post target, and copied and pasted this path to the server connect API directly in the browser. It then triggers the API and an empty save in the database and an empty mail.
I start the server connect API with a condition to check if a field post data is not empty , if not, continue with save to database and send out the mail. But somehow this condition is overruled or something? Here is the condition code and my question is how to prevent direct executing the api?
Condition CODE:
$_POST.con_bericht!='\'\''