We have issues from time to time with malicious users trying to game our system by using TOR. Upon investigation I can see that 100% of TOR visits lead to some form of abuse attempt. I see the benefits of TOR, and understand/support them, however in my case its not good traffic that comes in from it so it had to go.
So … although it’s a simple system to set up, I thought I’d put something together to show how I did it. I’m sure there will be better ways so pitch in anyone if you can see a better way.
We need two APIs, one to show the users true IP, the other to show a live list of official TOR exit nodes, note: there are other APIs out there that will list both official AND non official TOR exit nodes so feel free to use any others you find.
Required: Official TOR exit node list of IPs:
https://check.torproject.org/torbulkexitlist
Optional: Nice Geocode API (I use this a lot as it also includes currency symbols, location accuracy etc.)
http://ssl.geoplugin.net/json.gp
Note: to use https on the above you’ll need a cheap upgrade. Instead of the above you can also use Wapplers native $_SERVER.REMOTE_ADDR to find the users IP.
So, step by step:
- Create a test page using your chosen server model and save it - we’ll come back to this later
- Created a $_GET variable called userip - this will retrieve the Users IP address from the front end test page
- Create a Server Action - mine is called testtor
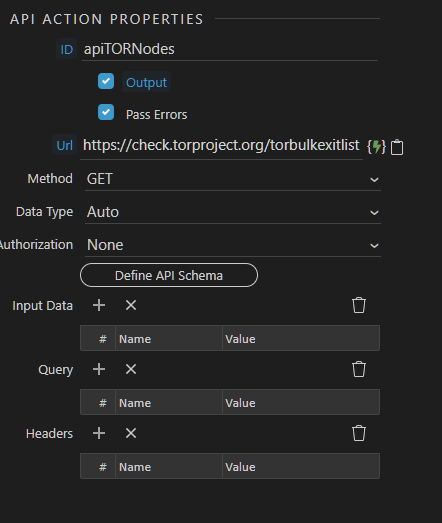
- Create an API action with an easy to identify name (good habit to have) - mine is called apiTORNodes. For the URL, add the TOR list: https://check.torproject.org/torbulkexitlist
- Select ‘Define API Schema’ -> ‘Fetch Schema’ -> then ‘Save’
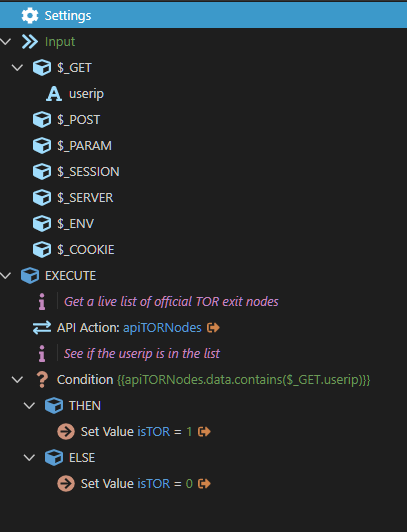
- Add a condition to find when the TOR node data contains the UserIP from the front end (see image below)
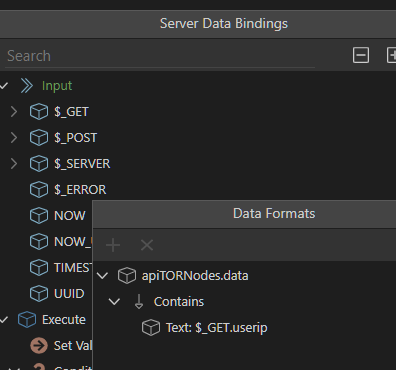
You should see this:
OK, we head over to the front end App Structure in our test page
- Add an API Date Source - I called mine apiUserIP
- Add the geoplugin URL then click ‘Define Schema’–>‘Fetch Schema’ - you’ll see data in the ‘data’ drop down, ‘geoplugin_request’ is the field containing the UserIP. Click ‘Save’
- Add a Server Connect with a memorable name - I called mine scTOR. Select ‘Server Action’ and include the server action you created earlier. Use the ‘geoplugin_request’ field for the userip in the ‘Input Parameters’
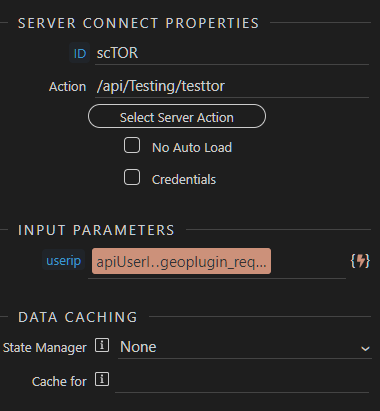
We’re all set up there, in your test page create a new paragraph and include two <span> in it. Add a Dynamic Attribute for both to show the result of the boolean value coming back from the Server Action:
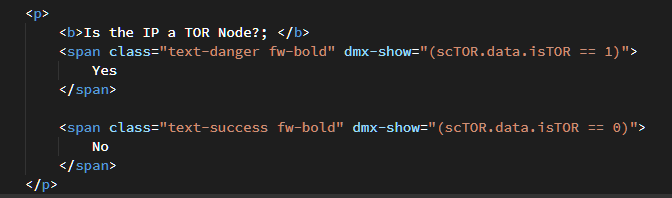
![]()
You can cross check your work by manually inputting a random IP taken from the TOR link above and putting it into your Server Actions condition instead of the actual UserIP.
Once happy you can add more logic to then redirect the user to somewhere else, record the IP, report to admin, flag it up somewhere etc. etc.
Very basic stuff but I’m sure it’ll help someone out there