Quick question. Does the CSRF token have an expiry and if so could we have the ability to set it? Appears that if the page is left open for a short while the token expires (we receive an error and have to refresh the page). Example. If we have an administration page open and make updates everything is fine initially but if we leave and come back and then try to make further changes we receive an error..?
Have you noticed if it happens no matter which method you use?
Meta tag or hidden input
We have only implemented it via meta tag usage so can't comment on the form input method. Have searched files for CSRF but don't seem to find any specific expiry period for the token.
For now we are going to turn it off as will cause dozens of User support requests. We just can't have this in a production environment just yet.
Experiencing the same issue @Cheese. Haven't tried yet with hidden input. Also, I'm having an issue with submitting medium editor content to the database. Getting a parse error which I'm wondering if it has something to do with the CSRF. Going to test once I turn off CSRF.
The CSRF token is valid as long as your session is active. So if the user is logged in the token is generated. When logged out session is cleared so next time new token is generated.
Could you explain what kind of user problems you have?
@George, mine was expiring while I was still logged in. That said, I was already logged in when I turned on CSRF. I'll try turning it back on, logging out and logging back in and see if it works.
Same as @TwitchBlade pretty much. Logged in User editing a record and on submit received the CSRF token error in the console. Have just cleared all cache from the server and locally and now running an extended test local and remotely. Will update you if the issue persists @George. Could be that Cloudflare cached older App Connect files but we do have a rule not to cache those critical to the Application in question (dmxAppConnect.js and config.js etc), and also this would not be a scenario we experience locally as not proxying via Cloudflare obviously.
Testing to see if logging back in after the setting is turned on works. Will keep ya'll posted.
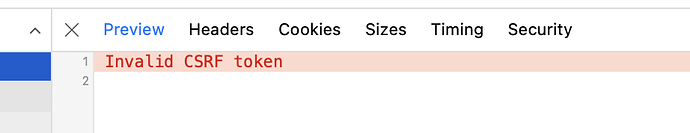
This one seems to be an issue.
I logged out and back in after turning the setting on and it still times out. I don't see the error guptast is getting. The only thing I get is this:
Seems to time out fast too.
Thats what i get.
The CSRF Token is stored in a session on the server, so when the session times out it will become invalid and a new Token must be generated. User login/logout doesn't matter. When you have a SPA and set the Token in a meta tag within the layout page it will never renew after a session expires since the layout page is not being reloaded anymore.
A new token is generated when a previous session was expired but that only happens server-side when a new page is requested. You could have a server action that generates a new token with some interval and bind that to the meta tag or just use the hidden form input which will generate a valid token each time the page is requested (it will expire when you leave the page open or have some caching active and the session expires).
Sounds to me like the metatag route is potentially problematic in the node environment and hidden fields is a more straightforward solution?