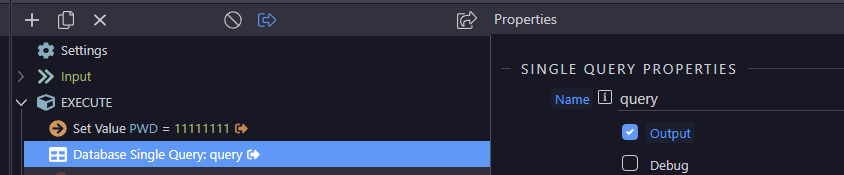
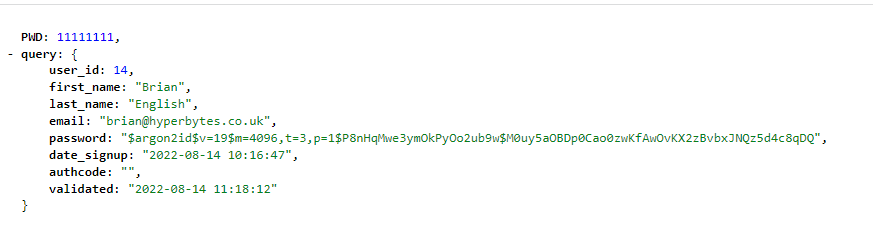
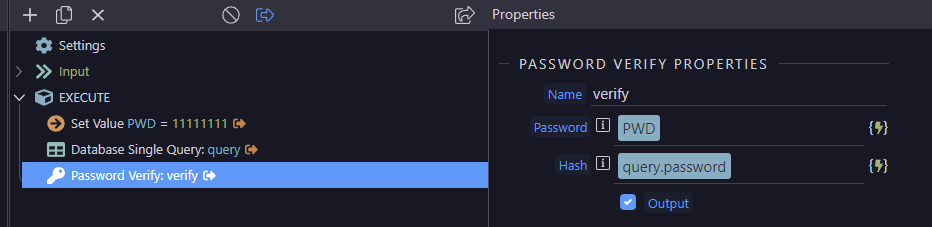
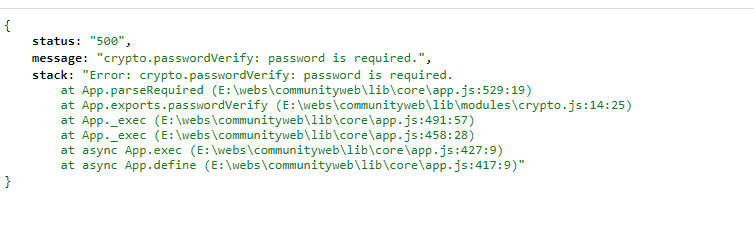
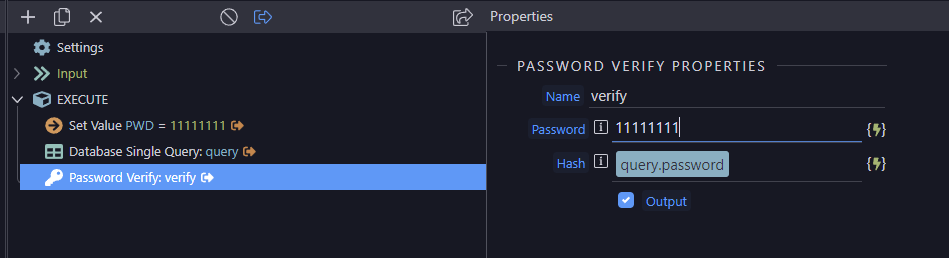
Sometimes I need to ask the user to renter a password just to verify they are the legitimate user before they perform critical actions such as changing passwords.
With SHA encryption this is easy as i simply hash the password and compare the sting to the stored string.
However, due to the nature of Argon, i believe this is not a valid method of confirmation
To date all i have been able to come up with is to perform an additional login step as a way of validating the password but I would prefer not to do this.
Is there a way of checking that a password entered matches an Argon encrypted password without a login step?
Also is there any documentation on Password Verify (is that the solution?) and Password Needs Rehash as i cant find any and I have no idea what they do.