So before using Argon2 I would have compared hashes in the Security Login.
How to approach using Argon2id? How does password verify fit here?
You are further on than me, i cant even find it in crypto section 
 It’s in the crypto formatters in the password hash option.
It’s in the crypto formatters in the password hash option.
It will output the following. Something like this
$argon2id$v=19$m=65536,t=4,p=1$aXY4ajIxUFhPMG9NYXdUWA$tbMa2mHYAMxptMxa7+XBMe7vM7U9j5qgHvj5oQWNadw
Where the first values are the argon2 used algorythm and some input parameters used. The password starts at p=1
First dollar sign is the salt (aXY4ajIxUFhPMG9NYXdUWA) and the second one is the hash (tbMa2mHYAMxptMxa7+XBMe7vM7U9j5qgHvj5oQWNadw)
You mean here?
Yup. Are you missing the last release? 2.6.4
NO, 2.6.4
Looks like it’s re-install time again
Reinstall fixed it.
@George any insights? Still no idea what to do to make Security login work with the new crypto hashing methods.
I have the feeling that this is something yet to be implemented.
Well there is a password verify formatter so with it and the stored hash you can implement the password login check.
Maybe @patrick can give you a sample
When I saw the new options, I did a bit of Googling and found this which looked useful. However it’s not related to Argon2 specifically, so it might not answer your question at all.
Well with bcrypt I believe you have the same issue. I haven’t looked in detail but I believe Security login component will compare two strings and if they are the same it will log you in.
But the password verify which is used by the new cryptographic methods is actually verifying the password so you will get a boolean returned which is of not much use right now in Security Login.
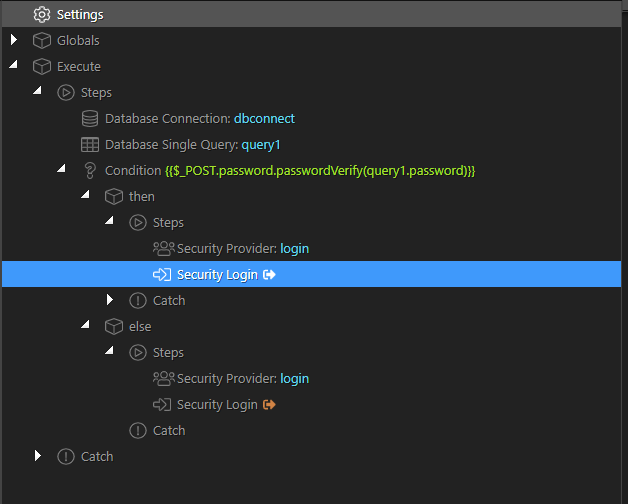
This works…query 1 retrievs the hashed password then the authentication happens in the condition, if successful it passes the right parameter to the login (the hashed password from query 1). If not it passes the wrong value.
It would be ideal to have an option in Security Login to choose the verification (compare or boolean) but this is a viable work around.
Thanks Simon! Witty workaround. I will implement it right now.
As you say an option that reflects the new crypto methods in Security login would be the way to go.
Thanks again!
Hi @sbecks
Are you getting a xml error on console following this approach? On unauthorized.
Just to double check with you before I open a bug report
Nice workaround, but in the else step I would just return a 401 status directly instead of calling the login.
Will investigate on how we could implement the passwordVerify into the security provider directly.
I am actually doing that. Returning 401 on the else but I am getting that xml error.
We do nothing with xml, all communication is done in json. Where exactly do you get the error?
Hey Guys,
Please check: