Hello,
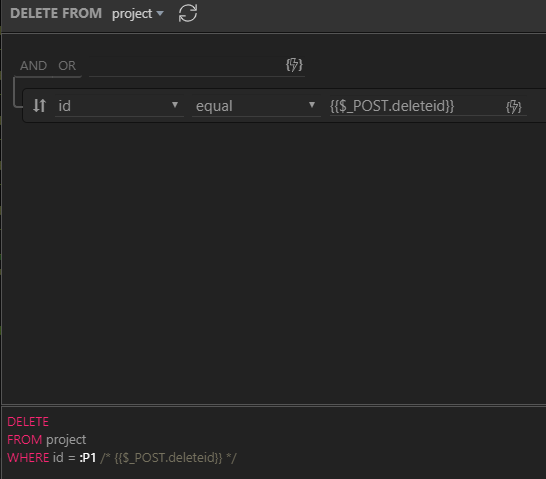
I have a modal that is integrated with a Data Detail component. I am able to open the modal and show the related record when I clicked on the Delete button from the table on the page. The input element is also able to show the ID of the record correctly. The form element is a Server Connect component that is (from what I know) correctly configured (based on several tutorials and videos I have found). The Submit button is on the Modal footer and is the child of the Server Connect form. The input element’s ID is set to the same POST variable (deleteid).
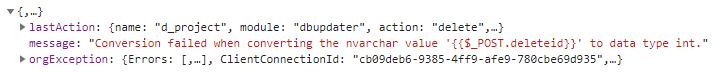
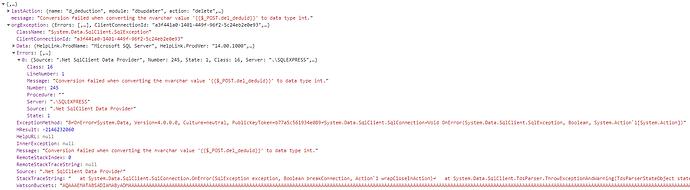
But when I click on the “Yes” button, it always returns HTTP status 500. Below is what I get from Google Chrome:
The error is:
“Conversion failed when converting the nvarchar value ‘{{$_POST.deleteid}}’ to data type int.”
The record ID is an integer in my database table.
I have already tried the following:
- Set the POST variable to “Number” from “Text”.
- Convert the deleteid variable to Number in the query via formatter.
- Changed the ID of the input element to something else.
- Changed the input type from hidden to text, then to number.
- Recreate the form element on the same page inside the modal.
- Created a new test page and created a new table. I have used a delete button directly without using a Modal and without the Data Detail component.
- Created a Condition in Server Actions.
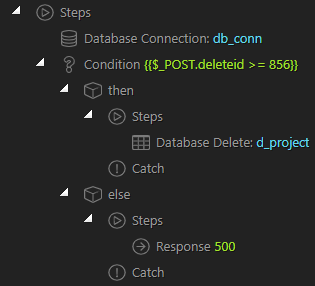
The record ID I tried to delete is 857, so it will pass the condition and to make sure it is a number. If tried to delete record ID 854, I am able to get the Error 500 and the text I have set in the response.
When ID is 857:
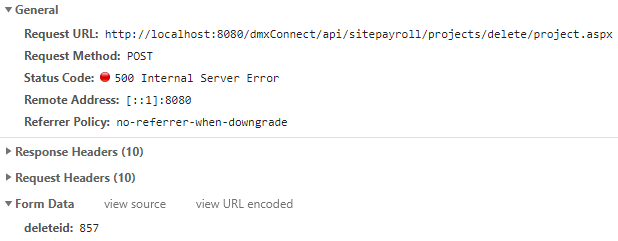
When ID is 854:
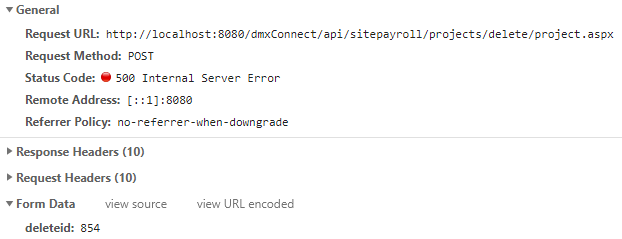
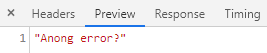
I am sure the record ID is being passed over to the query. I am not sure if the number variable is the same as the integer type in my database.
I am using SQL Server Express and using ASP.NET as the server model. My web server is IIS Express as my machine is a development workstation only.
I am able to insert/create records but haven’t tried updating any records yet.
I am not sure if this is a bug.
Please help.
Thanks in advance.