That makes sense. Thank you!
It’s a valid use.
Is it safe? No
Would I use it? No.
Would I build it if you paid me money? No. I have standards. 
Please guys. Do not encourage this horrible practice.
I have been following this thread to try and learn but it seems it has taken a couple different directions. Which horrible practice are you referring to? I’m kinda lost. 
This but ignoring the disclaimer.
The whole idea right from the start was a bad idea in a production environment, even just accessing the information_schema etc.
Just terrible from a security standpoint.
The only reason i had for even doing this in the first place was because i needed to find all image paths on a database I have not fully created, so I knew what tables had any dealings with images.
Now that I know what tables are used of the 50 I can target each properly.
The alternate would have been a mysql dump and find in a text editor of choice.
Just to clarify, I am in no way encouraging using this type of idea from my side, however in the same way that nuclear bombs were invented which was clearly a bad idea, many smart people used it’s research to create things like nuclear submarines which I suppose could be arguably good/bad. Therefore in the vein of knowledge expansion, its still valid information.
However I am for one very grateful for the warning labels you give us before I blow my own hands off.
The security issues around direct parameters make it dangerous.
That said, I am using it in an app. Although its an internal use app with security stuff in place, but its still dangerous.
The information_schema use case that you have @psweb, is exactly where I am using it too. But I found a way to use it in a manner that my inputs get “checked” before being run in the query.
0. Security Restrict!
- First, I set a custom query, and pass all the params that I am going to use - table name, column name etc. - via regular PDO Parameter mechanism to check agains info_schema table itself.
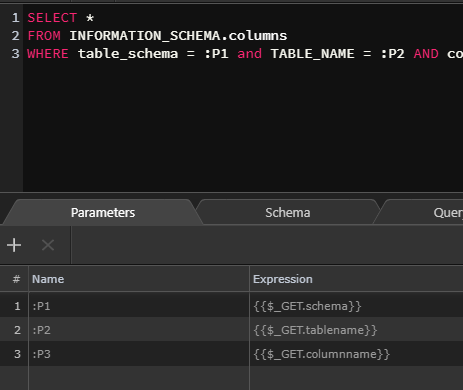
- Then I have a condition in place which checks if the output from above query matches the inputs or not.
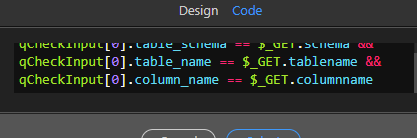
- In true part of this condition, I have the dangerous custom query with direct expression binding.
These steps ensure that the inputs will always be what I want them to be. So even in case of a security restrict compromise (although I am yet to see that happen in my Wappler projects), inputs will still be validated before the queries execute.
