So here is phase 1 or version 1 of my API , the authentication stage. Can’t believe it was so simple.
Comments/ feedback welcome
NOTE 1 I have not encrypted passwords to keep this tutorial simple however passwords should be encrypted in any deployed situation.
NOTE 2 You may want to set this up without the reversible password encryption until you have defined your schema api schema at the client side or generating the schema is difficult as encrypted parameters will need to be input
We will start with the data hosting site and write then server action.
We will be posting the data from the client site via an AI call using POST
The two sites have a shared key which is used for encrypting / decrypting the login details to add an extra level of security
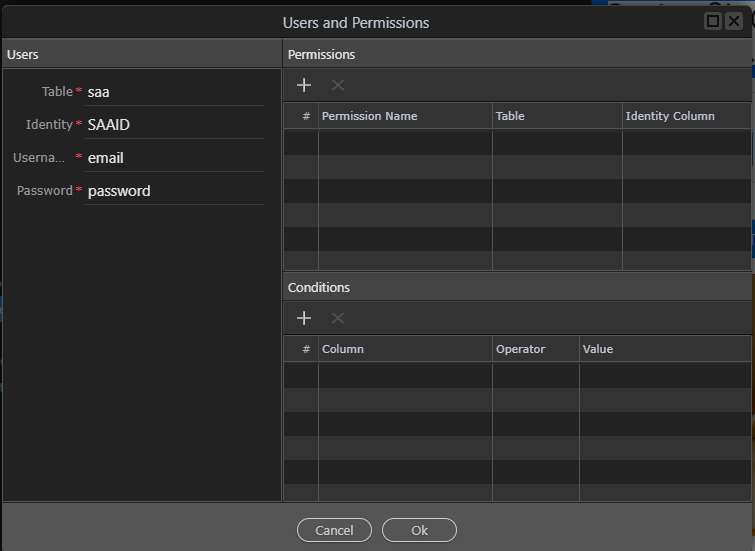
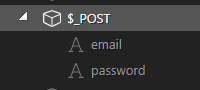
So let’s define our globals first, the parameters passed are email and password for use as a login
In this example the shared key is "@Wappler_Rocks@’
So we start by adding a standard server connection
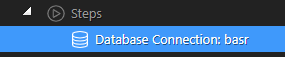
We then add a security provider. to keep things simple i do not have multiple roles defined but this would be possible in the normal way as all security restrictions will be applied at data server level
The security provider defines the fields used for login and the unique user identity to return, in this case SAAID
We now add a standard security login. REMEMBER, the email will be encrypted and will need to be decrypted using the shared key
So the username will be: {$_POST.email.decrypt("@Wappler_Rocks@")}}
and password will be: {{$_POST.password.decrypt("@Wappler_Rocks@")}} or when using password encryption {{$_POST.password.decrypt("@Wappler_Rocks@").sha512(“your_salt”)}} (based on sha512 encryption in this example)
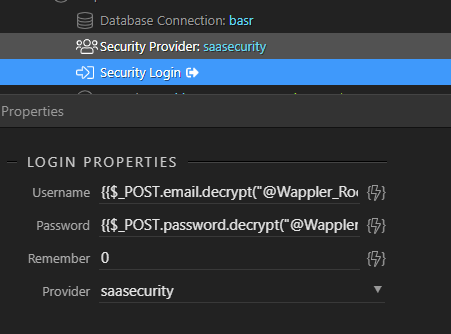
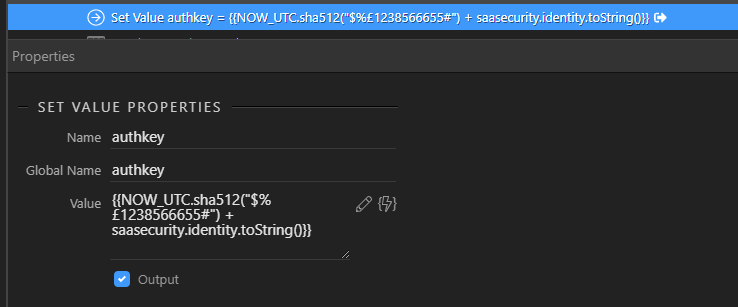
Now we generate a random authorisation token. I will do this by encrypting UTC_NOW with a salt and then adding the users Identity as a string to ensure the auth tokens cant be identical if two users perform an API request at exactly the same moment. We set the authkey to output as it will be needed by the client
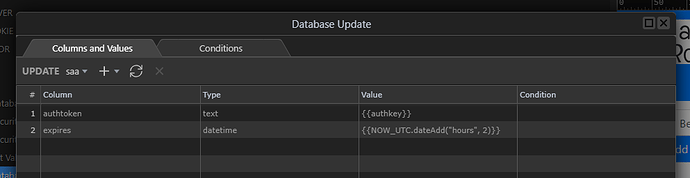
Now we simple perform a table update to store the auth key and expiry. As I am using sha512 encryption the auth key field should be large enough for the 128 character encryption key plus whatever is needed for the maximum length of the largest ID anticipated to be used.
So we simply insert the key and expiry time into the database table against the current logged in users record. I am using a 2 hour excpiry so the expression will be {{NOW_UTC.dateAdd('hours",2)}}
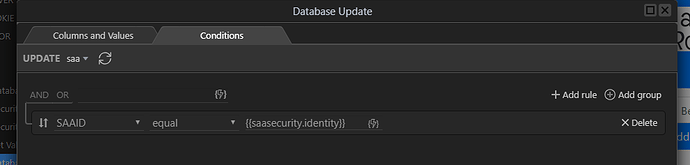
With the condition
That’s the API server side done!
Now over at client side we have a login form
Input names are email and password
Create you global POST variables
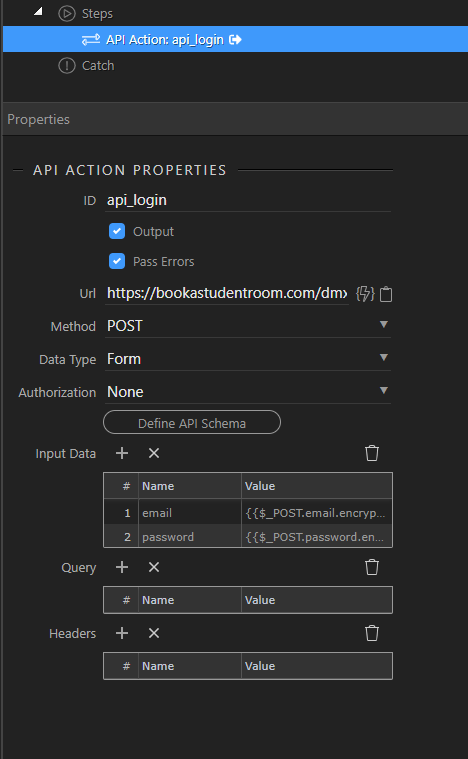
We now create an api call to the server
The url is simply the url of the server action on the data server (in my case using php, https://domainname/dmcConnect/api/server_action_name.php
The api call should be set to Method: POST
Data Type: Form
We send the email and password as login credentials but we must encrypt them first with encrypt with Password
so our parameters are
{{$_POST.email.encrypt("@Wappler_Rocks@")}}
and
{{$_POST.password.encrypt("@Wappler_Rocks@")}}
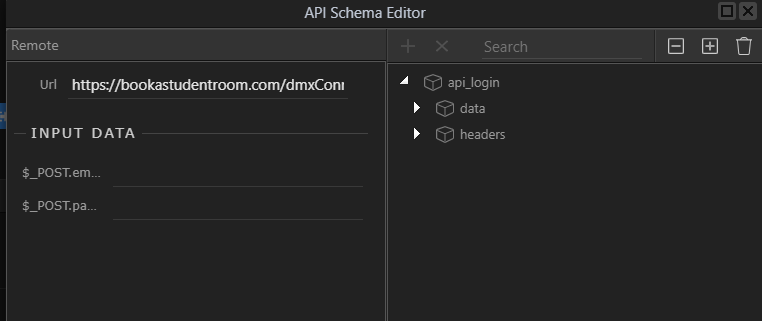
You can define your schema by entering the login details. You did take notice of my note at the start re generating the schema then adding the encryption?
Dont forget to make your form a server connect form and point it at this server action
Now within your form you can accept the authorisation token passed back from the API
On the success event of the login form you can pick up the authkey from the API output and store it by whatever method you want, (i will be using a cookie)
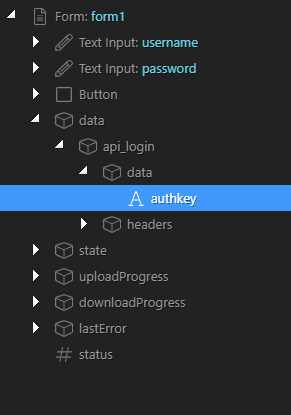
Failed logins can be handled in the normal way by using the “Unauthorised” dynamic event of the form
From this point i will be using that key to get the data by passing the key to the API server, where it will be used to filter the data for the user using the condition authkey={{authkey}} AND NOW_UTC < {{expires}}
MORE TO FOLLOW