Sure…see if these snips from our registration helps:
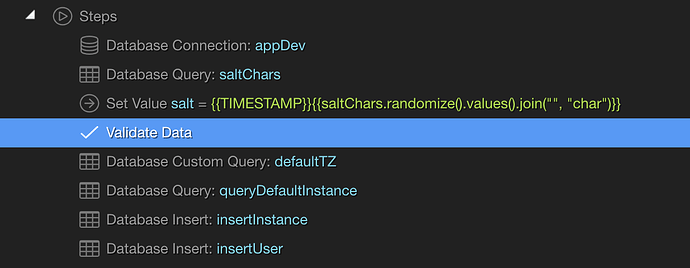
Registration
DB connection is a standard connection to db.
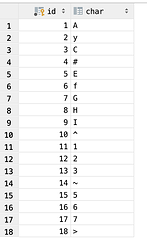
saltChars is a simple query to a database that has the following random content:
The salt value code is:
{{TIMESTAMP}}{{saltChars.randomize().values().join("", "char")}}
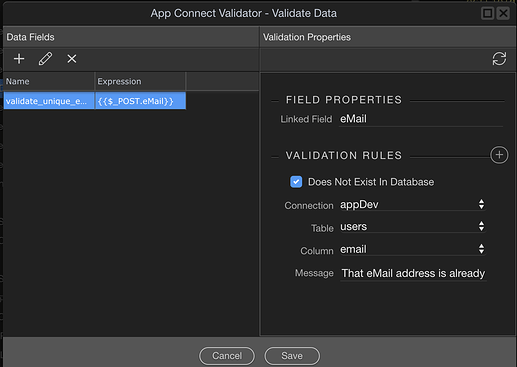
Validate Data just makes sure the email address is unique:
defaultTZ is just setting up a default time zone, so not really relevant for this…same with the defaultinstance and insertInstance actions.
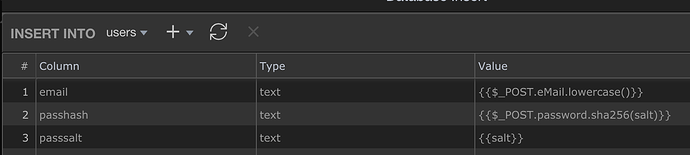
insertUser:
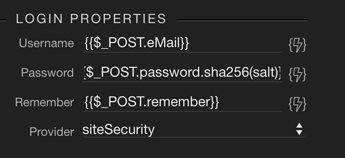
And then you use a login action to actually log them in:
Login after reg
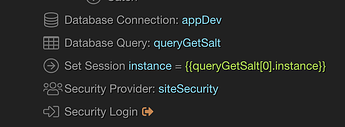
Again, standard db connector
GetSalt is just a query that retrieves the salt value stored for the user logging in…so lookup salt (I store that in a passsalt field) by email address, or username, or whatever.
instance again not relevant here.
And for Login, here is the code for the password:
{{pass.sha256(queryGetSalt[0].passsalt)}}
I think that’s it…Looking at this now, I suppose you could just use a timestamp and then randomize those characters instead of looking up the salt characters, but this worked for my first salting attempt.
–Ken