Hi.
We recently switched from SHA512 salt based password to Argon in one of our projects.
All our users would have to reset their password, which is fine.
We have a backend admin app (AA) and a consumer facing app (CA). Both use the same DB and user table in their security provider setup.
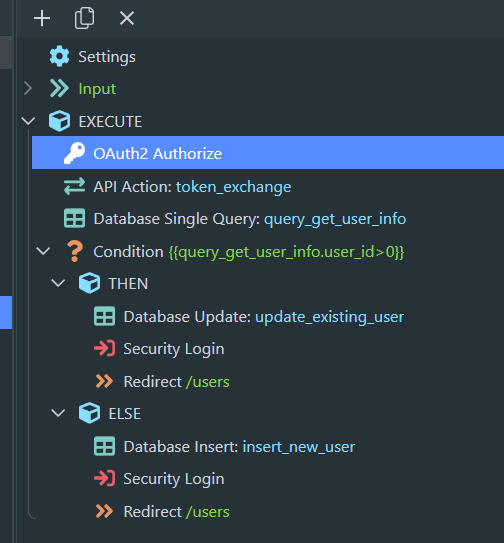
In one of our use cases, the admin user while logged into AA needs to log into the CA to view their user-dashboard. For this, we created a token based system where on click of a button in AA, user would be logged in CA.
The URL where we pass the token is a server connect route, like https://ca-domain.com/auto-login/:token
Based on this token, we would get the hashed password from DB via query.
Sending the DB password value in security login step, user is logged in.
But with Argon, now the security provider hashes this DB passed value again before checking against the DB value - which obviously does not match.
I understand that extracting original plain text password, or attempting to un-hash the argon string would be stupid. So what is the best way to approach this?
The security provider cannot be changed since the same provider is used elsewhere in the CA dashboard SAs which needs to work with its own login flow.
In a gist, we need to do security login without asking the user for the password on our CA.